6 Use Cases Based on DSPM Components
In this age of information technology, businesses have to deal with the growing need to generate and secure huge stockpiles of data. This is why it is more important than ever to have extensive and effective policies for handling and securing that data. Data Security Posture Management (DSPM) is one solution that enables modern-day organizations to implement comprehensive data security measures. In this article, you will discover DSPM use cases and learn how organizations can utilize DSPN solutions to ensure data security and compliance with data regulations.
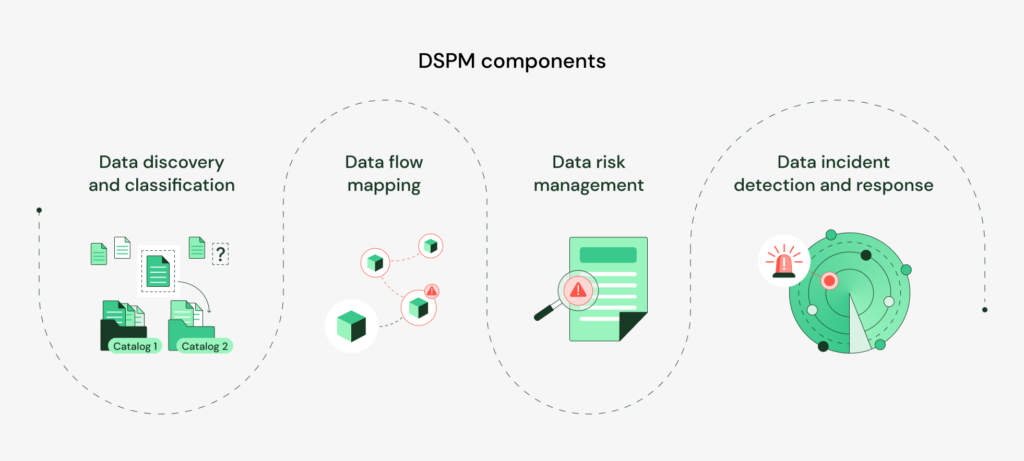
A DSPM solution is a mixture of procedures and technologies that empower organizations to take command of their data security. A detailed DSPM solution starts with data cataloging and goes to data flow mapping, risk management, and data incident detection and response.
A comprehensive DSPM solution will allow any organization to detect and respond to data security threats in a timely manner. Apart from this, DSPM also offers surety of compliance with regulations, constant monitoring of data security posture, and suggestions on where to improve it.
DSPM components
The key components of a complete DSPM solution are as follows:
- Data Discovery and Classification
- Data Flow Mapping
- Risk Management
- Data Incident Detection and Response.
Data discovery and classification
A general rule in security is that you can not protect what you do not know exists. If you are unaware of your assets, you are definitely not capable enough to safeguard them. This is why the first step of any DSPM solution is Data Cataloging, which involves discovering and cataloging all the data being generated and stored by an organization.
This process includes identifying and classifying data based on its sensitivity, such as Personally Identifiable Information (PII), Protected Health Information (PHI), and Payment Card Industry Data Security Standard (PCI-DSS) data. Data cataloging helps organizations get a clear picture of their data, which is crucial in managing and securing it.
Data flow mapping
This step involves tracking the movement of data within an organization and identifying potential vulnerabilities and exposure areas. By analyzing where the data is stored, who has access to it, and how it is being used, organizations can better understand how their sensitive data is being handled. Then, potential risks and vulnerabilities can be identified and resolved.
Data risk management
Risk Management means assessing the risks associated with an organization’s data and implementing security measures to mitigate those risks. This could involve implementing security controls and policies, administering regular security audits, and continuously monitoring for potential risks. Risk management is a crucial component in DSPM solutions as it helps organizations identify and resolve potential risks before they become an immediate threat to their data security posture.
Data incident detection and response
The last component of a DSPM involves detecting and responding to incidents that pose a threat to an organization’s data security. This could involve detecting and responding to internal threats, such as employees with malicious intent, or dealing with external threats, such as cyber-attacks from hackers. Data incident detection and response are critical for securing an organization’s data.
Below mentioned DSPM use cases are based on the above DSMP components. Let’s take a deep dive into each component with the help of a use case.
Use case 1: Automating data cataloging
In the first DSPM use case, we will discuss how the process of Data Cataloging can be automated to streamline data security further. Manually cataloging an organization’s entire data is not only difficult but also a very time-consuming process.
A manual data catalog involves asking different agents about the data they are working with. As there is no way to validate their response, this approach usually leads to errors. Another problem is that the agent might not be aware of the full extent of the data they are handling, so gaps in their knowledge will lead to gaps in the data catalog. Because of this, getting a clear picture of an organization’s data can be a difficult task.
Using DSPM, the process of analyzing an organization’s entire data becomes fast as well as accurate, as there is no room for human error. This is done by using data discovery tools that discover and classify all of the data being generated and stored across an organization. All of the data that is discovered is added to the data catalog. This catalog is then used to track the flow of this data within the organization, and this data flow chart can be used to point out potential risks along the data path.
Let’s say that during the data catalog process, the DSPM identified data that was being stored on an unencrypted database. The organization will be made aware of this fact. Then they can take action to resolve this security threat by either moving the data to a secure database or by securing the current database.
Use case 2: Facilitating compliance and auditing processes
Most of the time, multiple security standards and policies are operating in your area of operations, and ensuring compliance with each and every one of them can become a hectic task. For our second use case, we will discuss how a comprehensive DSPM solution can help your organization ensure compliance with any security standards and policies, such as the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and the Payment Card Industry Data Security Standard (PCI-DSS).
For example, the GDPR requires that an organization execute appropriate technical and structural measures which ensure data security. But what are appropriate measures? This is where DSPM comes in. A DSPM system will let you know if your security procedures and policies are up to the industry standard or not and thus ensure regulations to infrastructure policies.
Another requirement of GDPR is that in cases of data breaches, the organization is bound to report to relevant authorities within 72 hours. But what if the organization itself is not aware of the data breach? This, too, can be avoided with the help of a DSPM. Using real-time incident reporting proficiencies, the DSPM will not only inform you about a data breach in a timely manner, but you may as well be able to avoid the breach.
Another requirement of some security regulations is regular audits of an organization’s data security posture. Manually auditing the security posture is not only time-consuming, but it also requires resources. This process can also be automated using a DSPM which will not only ensure continued compliance with these regulations but will also save time and resources.
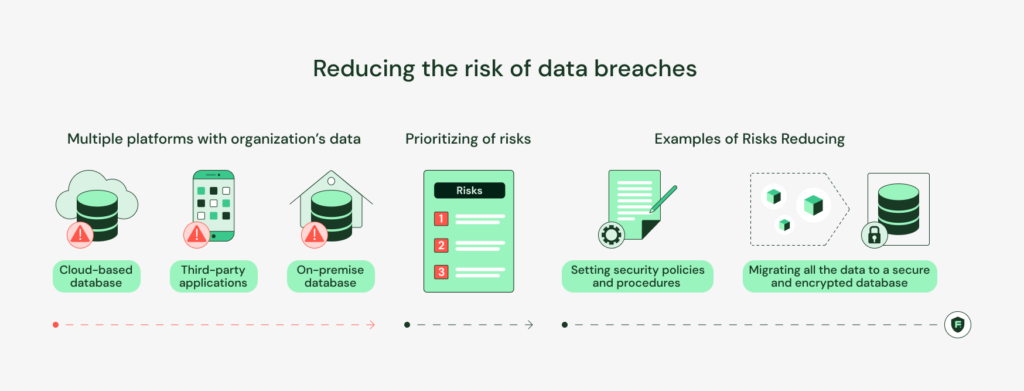
Use case 3: Reducing the risk of data breaches
Let’s see how a DSPM solution reduces the risk of data breaches in an organization. Usually, an organization’s data is present across multiple platforms, such as on-premise databases, cloud-based databases, and third-party applications. This data fragmentation makes it hard for organizations to secure the data at each end-point, which increases the risk of a data breach at the point of minimum security.
Using tools such as data flow mapping, a DSPM system enables the organization to track the movement of data from one point to another. Using this information, organizations can identify weak points where the risk of data breaches is maximum and take appropriate measures to minimize this risk.
Let’s say that the DSPM system points out that financial information is being stored in an unencrypted database. Or maybe it identifies that the organization was sharing sensitive data with external parties without proper security policies. This information will enable the organization to work on these weak areas where the risk of a data breach is maximum.
Organizations can then set proper security policies and procedures using information from the DSPM. In our example, these policies could look like migrating all the data to a secure and encrypted database or setting up security policies when sharing data with external parties. This way, organizations can ensure that their data is safe from breaches and focus on organizational goals rather than worrying about security.
In addition to identifying potential risks, DSPM can also be used to prioritize which risks to address first. This can help organizations to focus on the most critical risks and avoid spending time and resources on lower-priority issues. Among DSPM use cases, many organizations will position data risk reduction as the most prioritized.
For instance, a DSPM system may identify several potential vulnerabilities in an organization’s data security posture. By prioritizing these vulnerabilities based on their likelihood and impact, the organization can focus on addressing the most critical risks first and avoid wasting time and resources on lower-priority issues.
Use case 4: Internal threat, supply chain attack detection, and response
In this example, we will discuss how a DSPM system is used to detect and respond to internal threats within an organization. An example of an internal threat could be an employee trying to exfiltrate sensitive organizational data or your organization using a third-party library in its application. It is later found that the library was laced with a supply chain attack. In both these cases, the malicious agent has direct access to the organization’s data.
To protect against threats like these, a comprehensive DSPM system performs real-time data flow analysis. Data flow analysis means continuously monitoring the flow of data within an organization and keeping an eye out for unauthorized or suspicious data access activities.
For example, an employee with access to sensitive customer data downloads that data to a personal device without authorization. The DSPM system with real-time data flow analysis capabilities will detect this activity and alert the organization in a timely manner. This way, the organization can take appropriate actions before the employee gets out of bounds with the sensitive information.
Another example could be a third-party library being used by an organization’s application. Let’s say the library contains a supply chain attack that withdraws sensitive data from the organization. A DSPM system with real-time data flow analysis capabilities will detect that the library is accessing sensitive data and alert the organization in real-time. This allows the organization to take appropriate actions, such as removing the compromised library from the application.
In both the above scenarios, a DSPM helped organizations detect and respond to internal threats in a timely manner so as to avoid damage and protect their sensitive information from being compromised.
Use case 5: External threat detection and response
DPSM can also be used to detect and respond to external threats to an organization’s sensitive data, such as cyber-attacks for data breaches. This is done by continuously monitoring an organization’s systems and networks for potential threats and alerting the organization when a threat is detected.
For example, when a malicious data-theft attempt targets an organization’s website, the DSPM system will detect the attack and alert the organization. This allows the organization to take actions such as contacting law enforcement, implementing additional security measures, or shutting down their service temporarily until the issue is resolved, etc., to prevent the attack from causing damage.
Use case 6: Risk prioritization and reducing alert fatigue
In the last example, we will see how a comprehensive DSPM solution can help organizations avoid alert fatigue. By prioritizing the detected risks based on their sensitivity, DSPM systems allow organizations to focus on the most critical risks first and avoid spending resources on low-priority risks.
Let’s say a DSPM has identified several vulnerabilities in the data security posture of an organization. The system will also prioritize these vulnerabilities based on their probability of happening and their impact. Using this prioritization, the security team of this organization can address the most critical issues first and not get caught up with several low-impact issues.
Security teams often end up with alert fatigue because of the number of alerts in a big organization. Teams become overwhelmed by the huge amount of alerts being generated and fail to identify or respond to critical issues. But when all the risks have been pre-prioritized by the DSPM, this problem can be avoided, too, because employees can focus on critical issues without having to worry about meager issues.
This is how a robust DSPM solution can not only help an organization prioritize risks so that the most crucial issue is solved on a primary basis but also help the security teams avoid alert fatigue.
Conclusion
To wrap things up, we tried looking at DSPM use cases to better understand how organizations can utilize this solution to ensure data security and compliance with data regulations. We learned about different DSPM applications, including data catalog automation, ensuring compliance with security regulations, reducing the risk of data breaches, detecting internal/external threats, and avoiding alert fatigue.
All in all, DSPM is essential for organizations that intend to handle and safeguard their data efficiently. From providing complete visibility of an organization’s data to identifying potential vulnerabilities in their policies and procedures, DSPM enables them to identify threats before they become real and cause damage. This is how DSPM is shaping data security for organizations around the globe and helping them ensure that their data is being handled in a secure way.
If you are ready to take your DSPM journey to the next level, be sure to read through our blog post “5 Questions to Consider when Evaluating DSPM Solutions” for a comprehensive guide on the most important question to ask DSPM vendors.