DSPM vs. CSPM: Learn the differences and when to use each
In today’s digital landscape, data security is a top concern for businesses of all sizes. The amount of data being handled by organizations continues to grow at exponential rates. This means the need to implement effective tools and proper security strategies to protect this data from leaks and breaches becomes direr and direr. Two of the main solutions used for security management are Cloud Security Management (CSPM) and Data Security Posture Management (DSPM).
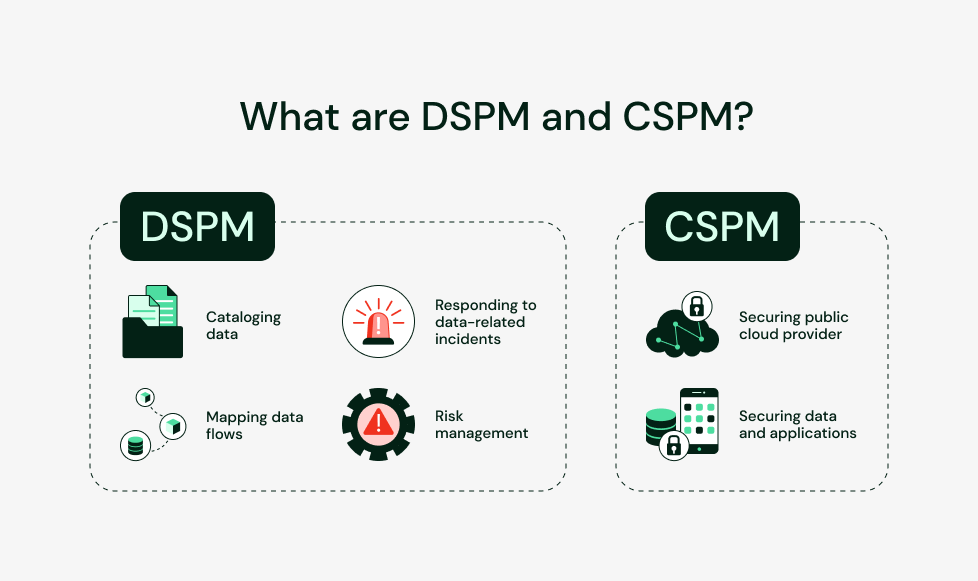
As the name suggests, Cloud Security Posture Management (CSPM) focuses on managing and securing the cloud infrastructure of an organization. Security by CSPM is limited to public cloud environments and does not include data-level protection. Data Security Posture Management (DSPM), on the other hand, focuses on securing and governing an organization’s data. It does not matter whether this data is stored on-premise or on the cloud. A typical flowchart of a DSPM includes data discovery and classification, mapping the flow of data, risk management for security and compliance, and data incident detection and response.
As a cyber security professional, you might be unsure of whether your organization needs CSPM, DSPM, or both. That is why we will take a detailed look at the key differences between CSPM and DSPM. We will also discuss the ideal cases where these solutions should be implemented and the benefits of implementing CSPM and DSPM together. Some pros and cons of each approach will also be discussed so that by the end of this article, you have a clear idea of both these solutions. Then you will be better equipped to decide whether CSPM or DSPM will be ideal for your organization.
What are DSPM and CSPM?
In the cloud and data domain, Data Security Posture Management and Cloud Security Posture Management are solutions for securing and managing an organization’s data and infrastructure.
What is CSPM?
CSPM refers to the set of practices and policies for securing the infrastructure of any public cloud environment. Typically this includes securing the workloads, services, networks managed by the public cloud provider, and data and applications hosted on the cloud. The main focus of CSPM is managing and securing the cloud environment rather than the data within it.
What is DSPM?
DSPM focuses solely on the privacy and security of the data, irrespective of the platform on which this data is present. Typically this includes discovering and cataloging data, mapping data flows, implementing risk management to ensure security and compliance, and continuously detecting and responding to data-related incidents. Unlike CSPM, DSPM is not limited to the public cloud and can be implemented in any environment where data is stored, accessed, and processed.
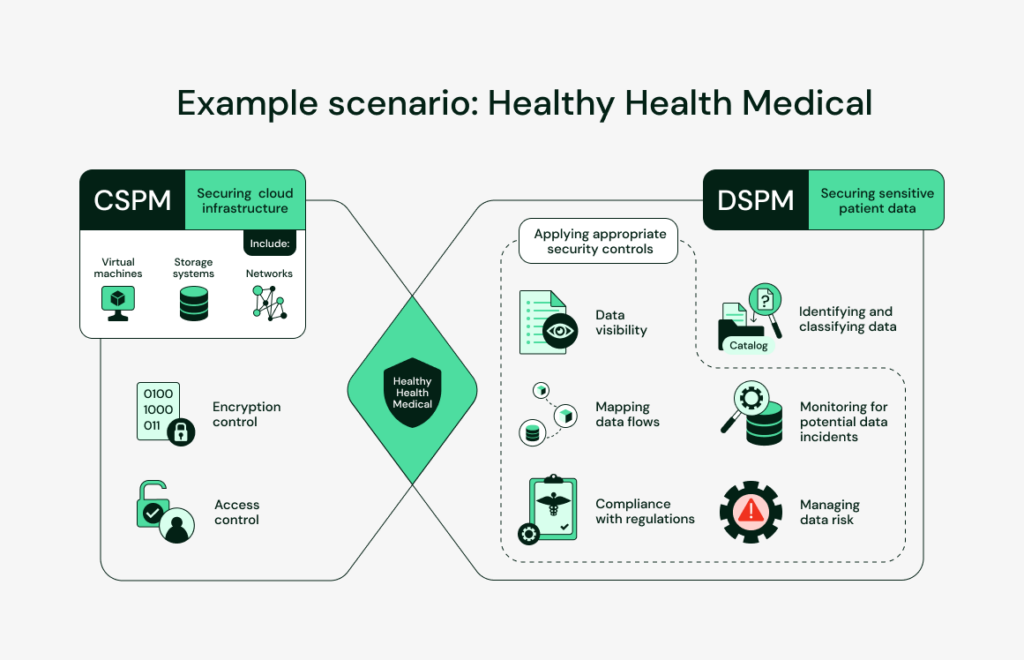
Example scenario: Healthy Health Medical
We are going to use an example to better understand how CSPM and DSPM work. Let’s see how a medical organization named “Healthy Health Medical” can use these solutions to secure their environments and data.
The security team of our example company can use CSPM to secure the infrastructure of their cloud environment, which includes virtual machines, storage systems, and networks. This can involve implementing encryption and access control policies to prevent unauthorized access to the cloud environment.
DSPM will be utilized by the company to safeguard the sensitive patient data that is stored on the cloud. This will involve executing a data catalog to discover and classify data based on its sensitivity and then administering proper security controls based on the classification of data. Let’s say this data catalog identifies Personally Identifiable Information (PII) or Protected Health Information (PHI). As this data is more sensitive, extra security controls will be applied to protect this data.
The data catalog will also help in data visibility i.e. help the company understand what data it has, where it is stored, and who has access to it. Then the company can enforce compliance with relevant regulations such as HIPAA, which requires that organizations protect PII and PHI.
Additionally, the company might also use DSPM to automate the management of data flow mapping. This will help understand how the data flows within the organization and across different systems. This will also help in identifying potential vulnerabilities and risks present in data management procedures. The company can then take security steps to mitigate these risks, such as implementing additional security controls or updating policies and procedures.
The company can also use DSPM to manage data risk. This will be achieved by implementing processes and technologies that identify, assess, and mitigate risks related to handling data. For example, DSPM can help assess the potential risks of sharing patient data with third-party organizations such as research institutes. The company can then implement data controls like encryption or access controls to mitigate the identified risks and ensure that data is handled in a secure and policy-compliant manner.
DPSM can also help the organization monitor for potential data incidents such as unauthorized access or data breaches. Utilizing intrusion detection systems or data loss prevention tools the organization could expose data incidents in real time and then take actions to either prevent or mitigate the effect of these incidents.
If Healthy Health Medical decides to use CSPM and DSPM together, it will be able to protect the cloud infrastructure as well as the sensitive data that is stored there. This way the organization will ensure the security of patient data as well as compliance with relevant regulations. The patients will rest assured that their sensitive data is secure with this organization and the organization can focus on providing high-quality medical care without having to worry about data or infrastructure security risks.
How do DSPM and CSPM work?
Both these solutions work in different ways to secure data or infrastructure.
Basics of CSPM
CSPM employs a combination of algorithms and technologies to monitor and control the infrastructure of a cloud environment. This could involve monitoring the use and access of resources such as virtual machines, storage buckets, and networks. And then implementing encryption and access controls to secure these resources.
CSPM functionality
CSPM solutions usually use Application Programming Interfaces (APIs) provided by the public cloud provider to gather infrastructure-related information and apply security controls. What this means is that CSPM will only be able to protect the infrastructure of a managed public cloud and not the assets that are stored in other environments such as on-premise data centers, private clouds, SaaS providers, or unmanaged data stores.
Basics of DSPM
DSPM utilizes a different set of algorithms and technologies to secure the data, rather than the infrastructure that it is present on. This could involve executing a data catalog to discover and classify data based on its sensitivity, and then applying security controls based on the classification. DSPM solutions also use data flow mapping to recognize how data flows within an organization. This data flow chart can help identify potential risks and vulnerabilities present in data handling methods.
DSPM capabilities
A complete DSPM solution can gather information about an organization’s data from multiple sources including analyzing data in real-time. This is very crucial as more often than not, data is fragmented and distributed across different systems and environments. Because of this data fragmentation, a single-source solution can not provide complete protection for this data.
A primary element of DSPM is data classification. This involves discovering and categorizing an organization’s data based on its sensitivity and importance.
DSPM implementation
After data classification is complete, DSPM solutions can apply proper security controls based on the classification. For example, the data that is classified as PII or PHI will be encrypted to protect its confidentiality. Or access controls might be applied to prevent unauthorized access to sensitive data. DSPM solutions must provide data flow mapping that will help in understanding how the data is flowing within an organization. The solution provider will also identify potential risks in the data handling procedures.
When should you use each one?
It is very important to keep in mind the specific needs and goals of your organization when deciding whether to use CSPM, DSPM, or both. Both these solutions have their strengths and limitations and are best suited to different scenarios.
CSPM for cloud infrastructure protection
CSPM is ideal in scenarios where the primary focus is protecting the infrastructure of a cloud environment itself. An organization moving to the cloud for the first time will need to ensure that its infrastructure is secure and security compliant before making the big move. Or an organization using multiple cloud services from different providers and wants to execute consistent security controls across these services. Using a CSPM solution would be ideal in situations like these.
For example, a financial services company is moving its data and applications to the cloud. By using CSPM to implement encryption and access control across the cloud infrastructure, the company can prevent unauthorized access to the data and applications that are running on the cloud environment. It will also help them protect the confidentiality and integrity of sensitive financial data.
DSPM for data protection
DSPM solutions are ideal for situations where the primary focus is securing the data itself, rather than the infrastructure this data runs on. An organization that has large amounts of sensitive data and wants to secure it can utilize a DSPM solution to achieve this. Or an organization subject to strict regulations could utilize DSPM to ensure compliance in handling sensitive data.
For example, a healthcare company that handles patient data on the cloud can use DSPM to implement a data catalog and data flow mapping. This way, the company will have a better understanding of the data it has, the storage points of this data, and who has access to it. After this, the company can ensure that this data is being handled in a secure and compliant manner at each point. DSPM can also help the company monitor data incidents and respond to them in real-time.
Combining DSPM and CSPM
An organization might need to utilize both DSPM and CSPM solutions to protect its digital assets. This could be the case if an organization has a large amount of sensitive data that is stored on the cloud and wants to implement both infrastructure-level and data-level security controls.
Some CSPM providers also offer DSPM solutions, but most of the time these solutions are superficial and only focus on data stored in a public cloud. In contrast, a purely DSPM solution will not be limited to the public cloud and thus, provide more rigorous protection for sensitive data.
For example, a financial company storing customer data on the cloud might use:
- A CSPM solution to execute encryption and access controls for the cloud infrastructure.
- A DSPM solution to implement data catalog and data flow mapping in order to safeguard sensitive data.
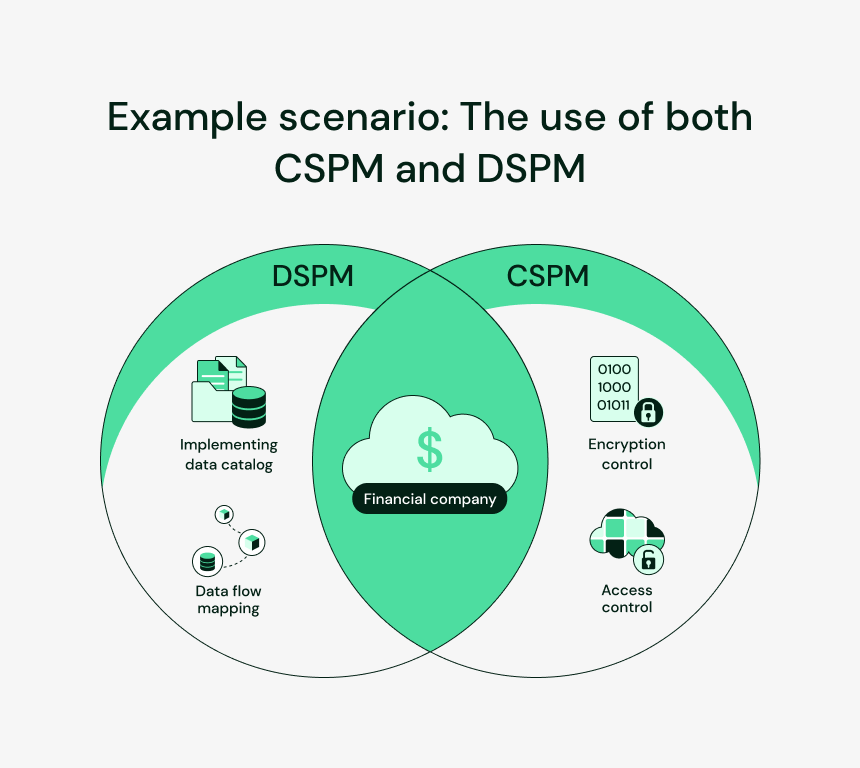
By utilizing both these solutions together, the company will be able to safeguard the confidentiality and integrity of its customer data while also ensuring that it is being handled in a secure manner.
Another example could be an organization that is subject to numerous regulations which have different requirements for data protection. In this case, this organization could use:
- A CSPM solution to implement infrastructure-level controls that fulfill the requirements of one set of regulations.
- A DSPM solution to implement data-level controls that fulfill compliance requirements of another set of regulations.
Let’s say a healthcare company is subject to both HIPAA and the General Data Protection Regulation (GDPR). This company might use
- A CSPM to implement encryption and access controls to secure patient data.
- A comprehensive DSPM solution to implement data catalog and data flow mapping in order to ensure that data is being handled in HIPAA and GDPR-compliant ways.
Can DSPM and CSPM be implemented together?
The short answer is yes. And most of the time, it is highly recommended to implement both these solutions. Together these solutions provide a more comprehensive and effective approach to protecting digital assets in the cloud environment. When executed together, these solutions harmonize with each other and provide a detailed and complete picture of an organization’s security posture.
Implementation of both DSPM and CSPM
By using APIs to exchange information between the two solutions, both DSPM and CSPM can be implemented together. For instance, a CSPM solution will use APIs to gather information related to the infrastructure of a cloud environment and apply security controls. A DSPM solution used alongside could access this information using APIs and then utilize this information to get a clear understanding of risks and vulnerabilities associated with handling data in the cloud environment.
Prioritizing risks and alerts
One particular scenario where DSPM and CSPM can enhance each other is using DSPM to prioritize alerts. DSPM solutions use algorithms to assess the potential impact of risks and incidents and then prioritize them based on their severity and probability. This helps to reduce alert fatigue as only the most important and urgent risks and vulnerabilities are brought to the attention of security teams.
Improving remediation efficiency
Using both DSPM and CSPM can significantly improve the efficiency of the remediation process for risks and incidents.
A DSPM solution can provide detailed information for each risk and incident including:
- Information about data involved in these incidents.
- Potential impacts of these risks and incidents.
- Steps that can be taken to prevent these incidents from occurring.
This enables security teams to quickly recognize the situation and take swift actions to resolve the risk or incident.
Generally, implementing both DSPM and CSPM together provides a complete and functional approach to securing the digital assets of an organization.
Pros and Cons
Both of these solutions have their own advantages and disadvantages. Organizations should keep these factors in mind while deciding which solution is best suited for them.
Advantages of DSPM
One major advantage of DSPM is that it provides better protection for sensitive data. Algorithms used by DSPM solutions discover and classify data and then apply suitable controls based on the classification. This ensures that sensitive data is protected and handled in a compliant manner.
Disadvantages of DSPM
One drawback of using DSPM is that it is a complex solution. Technical expertise is often required to implement DSPM solutions. Moreover, it may also require additional data processing and storage resources. This makes DSPM expensive as well as difficult to deploy when compared to CSPM. When deciding on a DSPM vendor, ask them about the resource consumption of the tool. This way you will have an idea of what to expect in your bill.
Another drawback is that some DSPM solutions only focus on data stored in public clouds and will not provide protection for data present in other environments. This greatly limits the effectiveness of DSPM in securing fragmented data. Make sure that your DSPM provider’s coverage fits your organization’s needs before deciding to hire them.
Advantages of CSPM
One advantage of using CSPM is that these solutions can monitor and control the use of resources like VMs, storage systems, networks, etc and implement controls to limit or safeguard access to these resources. This helps ensure the availability, integrity, and confidentiality of a managed public cloud infrastructure.
Disadvantages of CSPM
A disadvantage of CSPM is that it fails to provide as detailed protection for sensitive data as DSPM. As the primary focus of CSPM solutions is the protection of public cloud infrastructure, they are unable to provide comprehensive protection for data that is stored on this infrastructure. This tends to leave gaps in an organization’s security posture and increases the risks of a data breach.
Conclusion
In conclusion, DSPM and CSPM are different approaches aimed at protecting digital assets in this age of information technology. The main focus of DSPM is securing the data while CSPM focuses on securing the infrastructure of the public cloud where this data is present.
Both these solutions have their own advantages and drawbacks, and organizations should carefully consider these elements before finalizing which solution to implement. Generally, organizations need to implement both solutions together in order to provide a comprehensive and effective approach to safeguard data and infrastructure.
DSPM vs CSPM? You probably need both. If both solutions are implemented together, organizations can not only maintain the integrity of sensitive data, but they can also ensure that it is being handled in a secure and compliant manner. This leads to a reduced risk of data breaches and sustains customer trust in the organization.
Overall, DSPM and CSPM are vital for safeguarding an organization’s data and cloud infrastructure. The only thing to keep in mind is your organization’s needs before deciding on which solution or combination of solutions is best suited for your needs.