Flow immediately surfaces a new sensitive data flow detected from a service called “analytics” to Salesforce
Why Flow
Flow is the only data security platform that analyzes both data at rest and data in motion so you regain control over all your data.
Can your data security platform recognize this leakage?
Data flow analysis identifies that the origin of the data leakage is an unmanaged and misconfigured database
Action is taken and solved directly
with the asset owner.
Flow’s data security platform combines Data Security Posture Management (DSPM) together with real-time detection and response to data security violations.
Automatically discovers all your data – at rest and in motion
Automatically classify
your data
Manages and tracks
your data security posture
Detects and responds to data violations
Both data at rest & data in motion.
That’s what sets us apart.
Full coverage. Yes, even for on-premises, applications and SaaS.
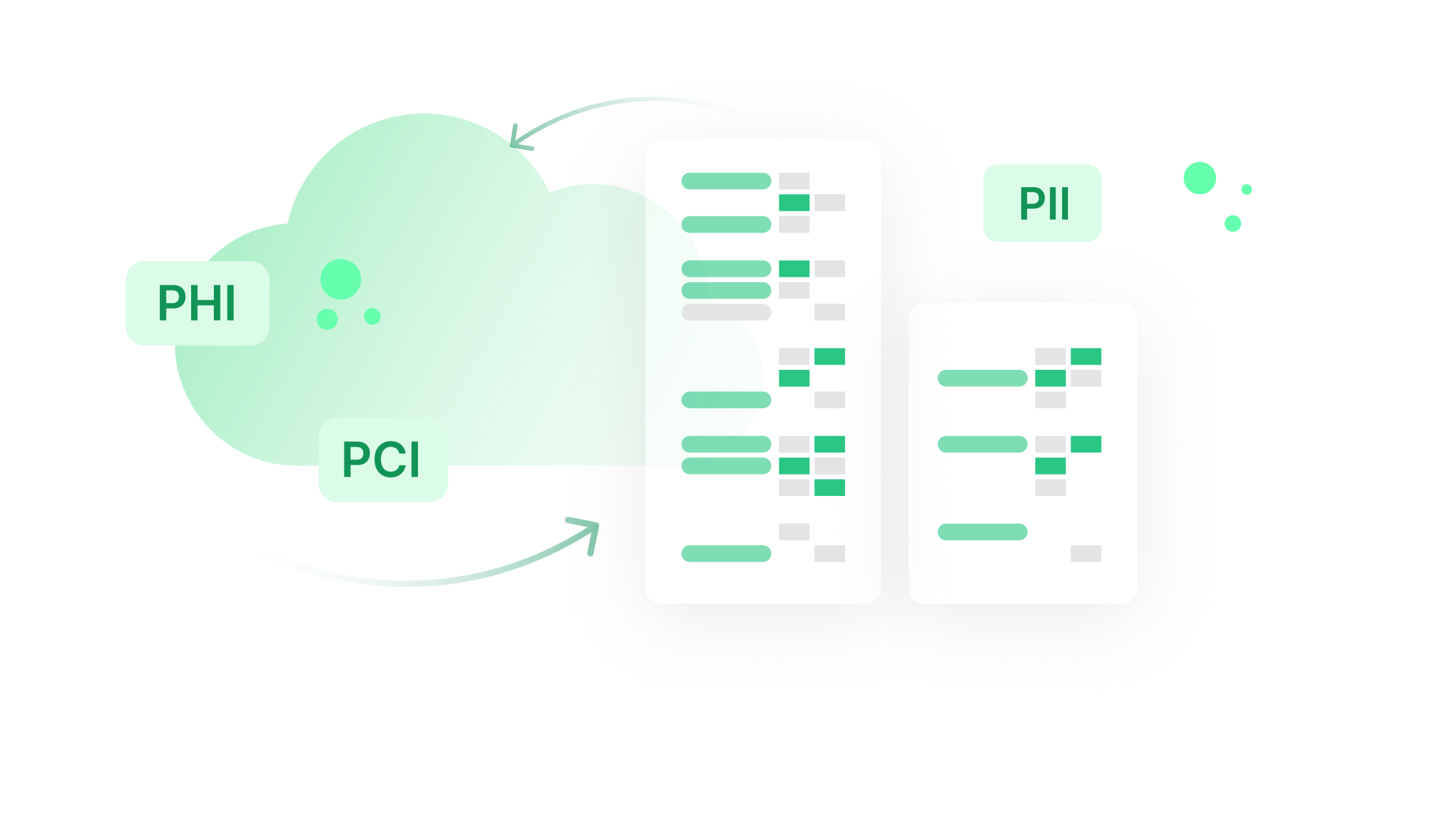
Data security coverage in all data stores and across all your environments, including: your managed and unmanaged data stores, stored and processed data within the cloud, on-premises and SaaS environments.
Example: Data that is accidentally sent to Salesforce through an API is only detected by analyzing data in motion
Next-level classification enriched with context.

Your data is not only data. It has application and business context, which only data in motion can provide for precise classification.
Example: “just an email address” becomes a European email address and more so, you know if it was generated by an insider, a contractor, or is from a bought list.
Root-cause analysis for effective remediation.
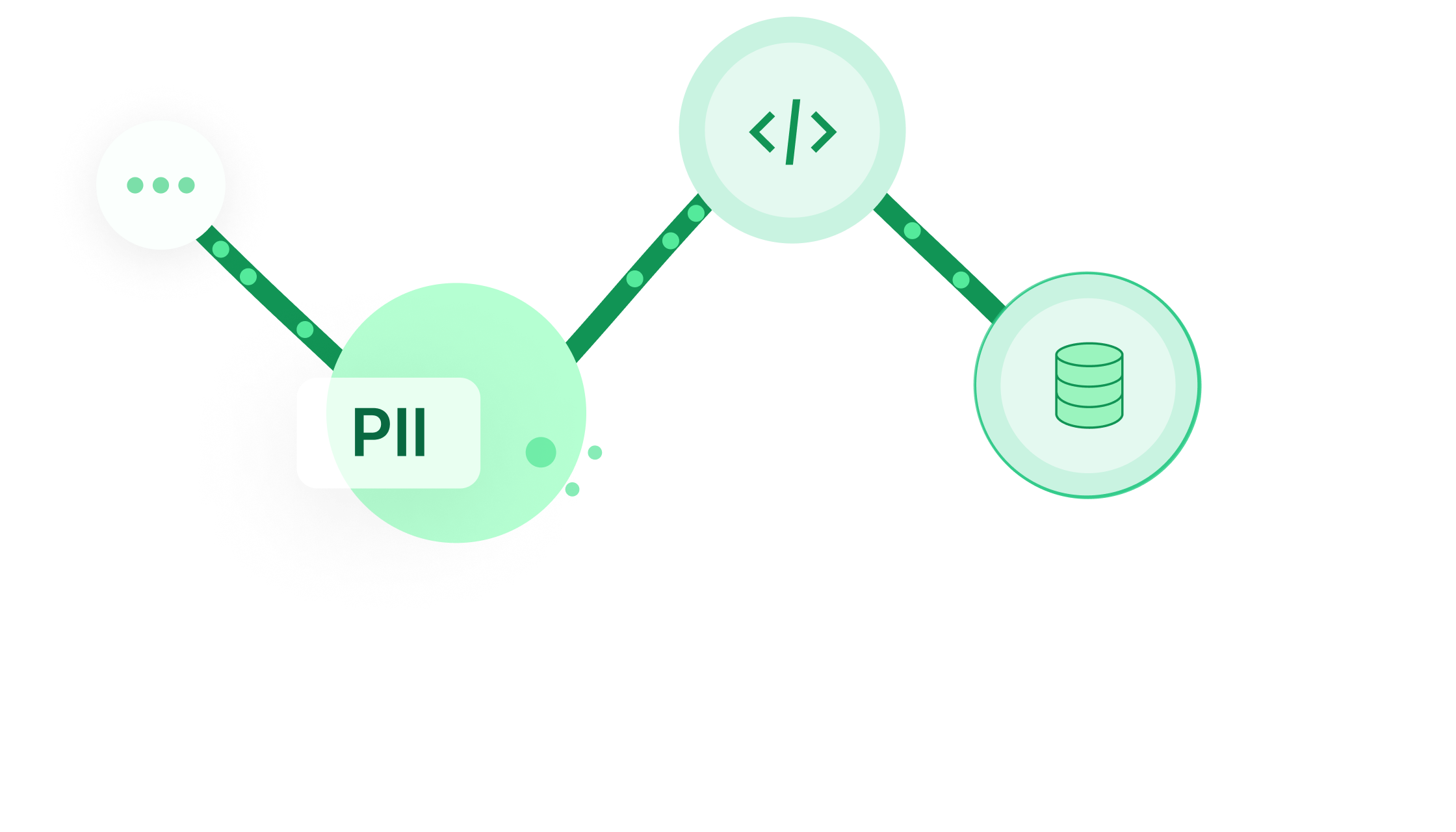
Forget that overreliance on engineering teams. When a security violation occurs, analyzing data in motion at runtime gives you the full story so you can efficiently and effectively remediate: the data source, the application that is accessing or processing the data, the data owner, and the full journey of the data.
Example: When finding PII in a SaaS-based data store which receives data from thousands of applications, you need to prevent that leakage from reoccurring by rolling back the data journey, finding its origin and its data owner.
Data violation detection and response. In real time.
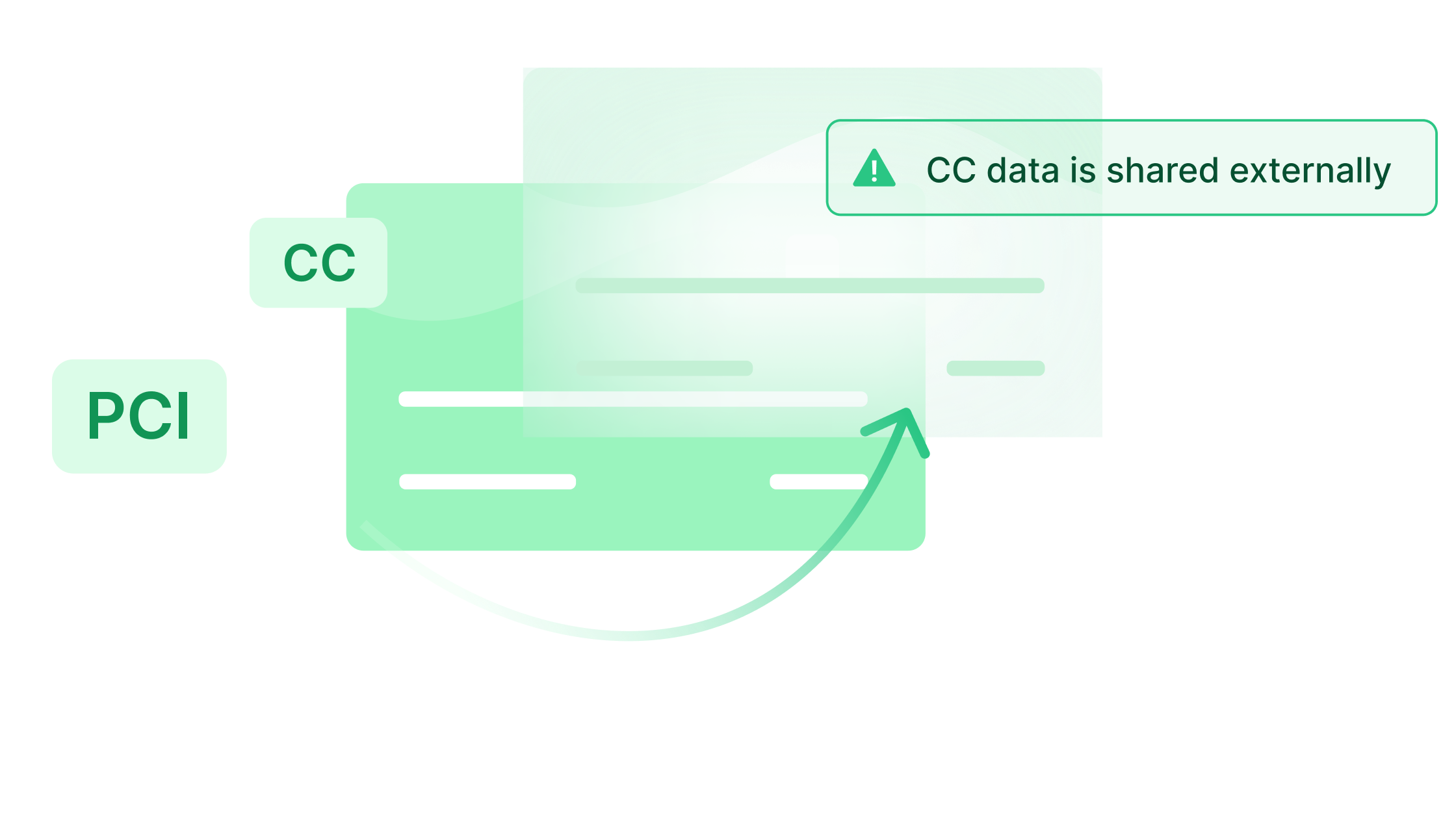
When the data is stored in the wrong place, it’s already too late. Analyzing data in motion at runtime lets you enforce your security policy and if a violation does occur, you get alerted in real time. More so, the provided granular data gives you all you need to effectively respond.
Example: A supply chain attack in the PCI environment causes credit card numbers to be shared outside of the card data environment. You know immediately all the data required to respond.
Continuous monitoring. But with reduced cloud security billing expenses.
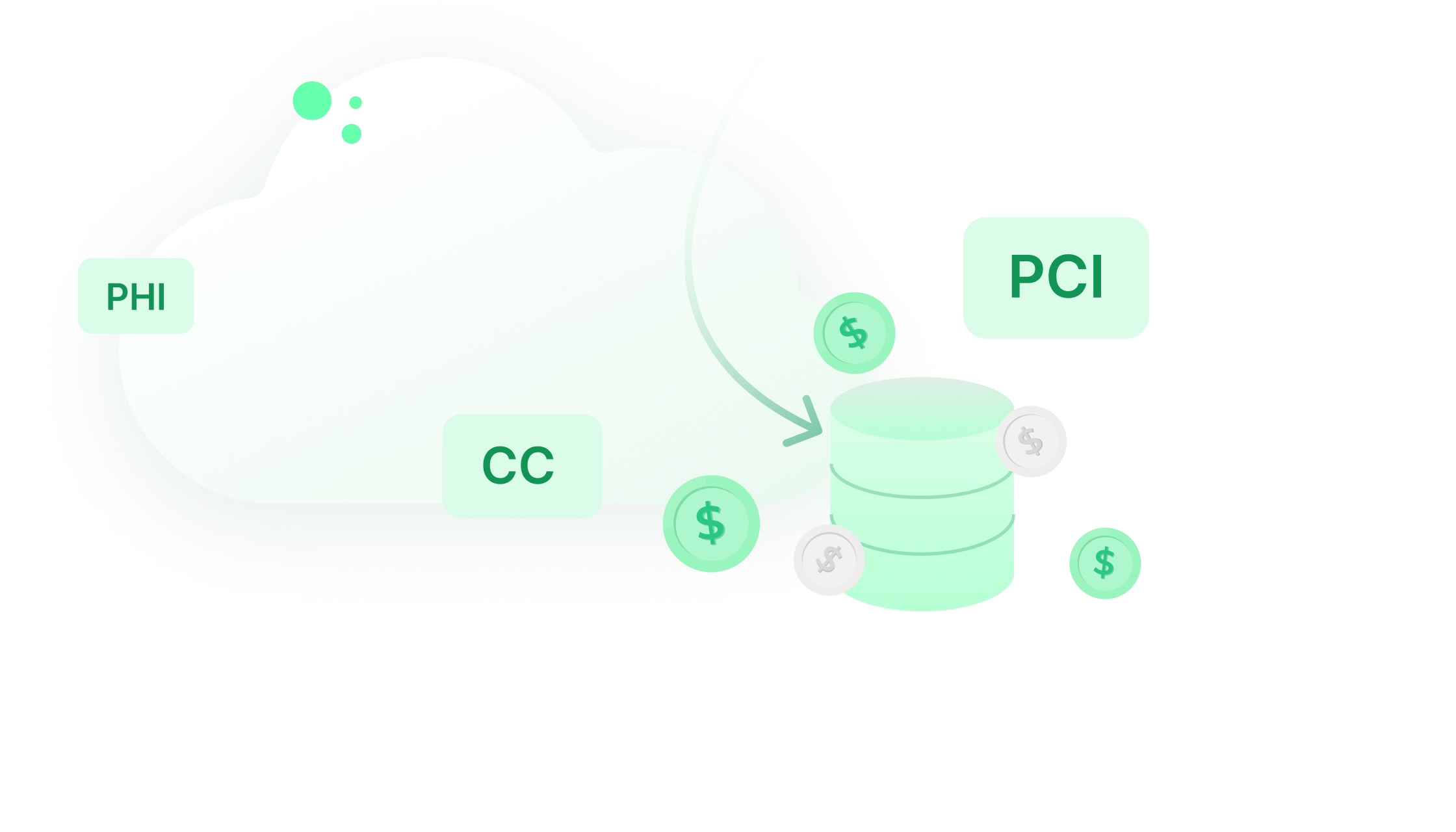
Full database scanning is expensive. Continuous monitoring of data in motion means that violations are identified when data is passed on the wire, reducing the need for periodic comprehensive scanning.
Example: When looking just at data at rest, knowing if PHI was leaked from an application to a data lake, means the copying and processing of petabytes of logs, leading to millions of dollars in cloud billing expenses – eventually making scanning an infrequent task.
Data security coverage in all data stores and across all your environments, including: your managed and unmanaged data stores, stored and processed data within the cloud, on-premises and SaaS environments.
Example: Data that is accidentally sent to Salesforce through an API is only detected by analyzing data in motion

Your data is not only data. It has application and business context, which only data in motion can provide for precise classification.
Example: “just an email address” becomes a European email address and more so, you know if it was generated by an insider, a contractor, or is from a bought list.

Forget that overreliance on engineering teams. When a security violation occurs, analyzing data in motion at runtime gives you the full story so you can efficiently and effectively remediate: the data source, the application that is accessing or processing the data, the data owner, and the full journey of the data.
Example: When finding PII in a SaaS-based data store which receives data from thousands of applications, you need to prevent that leakage from reoccurring by rolling back the data journey, finding its origin and its data owner.

When the data is stored in the wrong place, it’s already too late. Analyzing data in motion at runtime lets you enforce your security policy and if a violation does occur, you get alerted in real time. More so, the provided granular data gives you all you need to effectively respond.
Example: A supply chain attack in the PCI environment causes credit card numbers to be shared outside of the card data environment. You know immediately all the data required to respond.

Full database scanning is expensive. Continuous monitoring of data in motion means that violations are identified when data is passed on the wire, reducing the need for periodic comprehensive scanning.
Example: When looking just at data at rest, knowing if PHI was leaked from an application to a data lake, means the copying and processing of petabytes of logs, leading to millions of dollars in cloud billing expenses – eventually making scanning an infrequent task.

Can’t Wait to See What Flows?
"*" indicates required fields