Enterprises Run on Data.
We Secure it,
at Runtime.
Flow discovers, classifies and prevents data leaks at
every state, every stage, and everywhere
Step into the future of data security
Enterprise-grade protection. Seamless deployment.
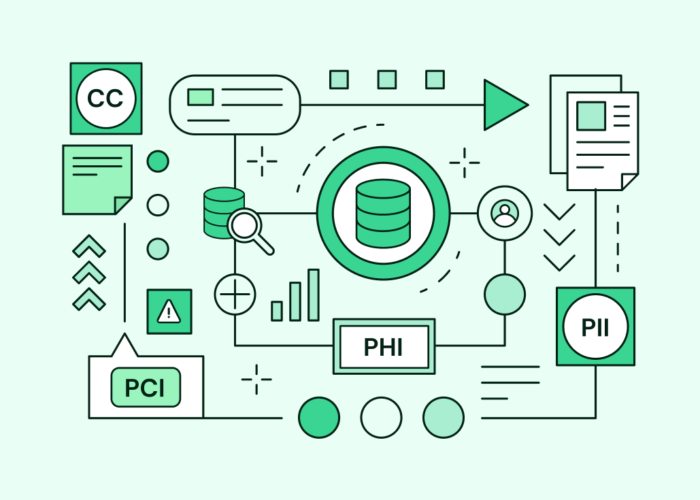
Data discovery & classification
Catalog all your data instantly, whether structured or unstructured. Flow’s LLM-powered classification automatically identifies sensitive information such as PII, PCI, and PHI, all without extracting data from your environment
Data loss prevention
Prevent data leaks in real-time with runtime policies and enforcement. Flow actively safeguards your data, ensuring it remains protected from unauthorized access and misuse.
Data security posture
& risk management
Identify data risks in real-time, including exposures, mishandling, access, network, and cloud issues. Seamless integration with collaboration and ticketing tools, streamlining remediation.
Flow brings Runtime to the party!
Automatically discover, classify, and prevent data leaks in every state – at rest, in use and in motion
60
seconds to full
data discovery
94
%of data taken out of
the
shadows
100
+cloud providers, datastores and integrations