The Art Of Protecting Sensitive Data:
Data Security Guide


Over the years, engineering and technology have transformed rapidly, generating and processing a vast amount of data that needs to be protected, as the risk of cyberattacks and breaches is high. To safeguard enterprise data, organizations must take a proactive approach to data security, learn about the best practices to protect data and use the necessary tools and platforms for data security.
This article will explore what sensitive data is, guide you through some fundamentals of data security, discuss the risks and challenges of data breaches, give some best practices for keeping sensitive data safe, and explain how using a data security platform can ensure sensitive data is protected.
Understanding Sensitive Data
Sensitive data is any type of information processed or stored by an individual or organization that must be kept confidential and away from unauthorized access or disclosure.
Data is considered sensitive if it contains information that, if disclosed carelessly to unauthorized parties, can lead to severe consequences such as identity theft, financial loss, legal penalties, etc.
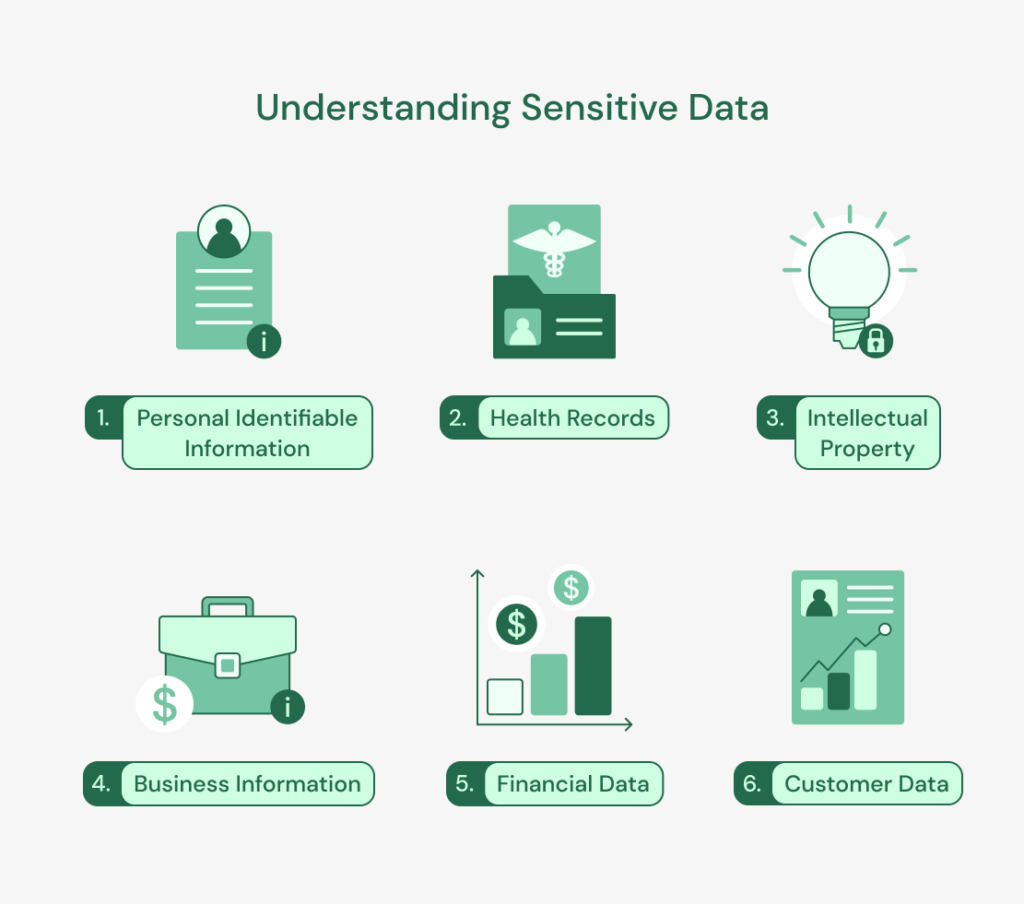
Common examples of sensitive data include:
- Personal Identifiable Information (PII): includes any data explicitly used to identify an individual. They consist of an individual’s address, name, driver’s license, social security number, passport number, and other information like biometric data. They’re considered sensitive data because attackers can use them to impersonate someone; hence, they must be protected.
- Health Records: This includes any data related to an individual’s mental or physical health, such as medical diagnoses, laboratory tests, and medication history. They’re usually protected by laws and regulations and processed only by medical professionals bound by the obligation of medical secrecy.
- Intellectual Property: Intellectual property (IP) refers to the creations of the mind, which can be an invention, artistic works, patents, trade secrets, or literary works. IP is usually considered sensitive because unauthorized access or disclosure can lead to lost revenue, financial loss, and damaged reputations for individuals and businesses. For example, wrong access to a company’s patent by a competitor can lead to the inability of the company to compete in the market, as competitors can quickly produce the same product or service without incurring costs associated with research and development.
- Business Information: Certain business information, like business plans, financial information, investments, trade secrets, customer data, marketing strategies, etc., is considered sensitive because it is critical to the organization’s success. Wrong access to sensitive information about the business can lead to damage or financial loss. This is, for example, why most companies require new employees to sign Non-Disclosure Agreement (NDA) to protect the business information and ensure confidentiality from their own employees.
- Financial Data: Information such as bank account numbers, bank statements, and credit card numbers is sensitive data that’s usually targeted by cybercriminals to commit fraud and other mischief. Strict measures must be taken to protect financial data to avoid unauthorized access.
- Customer Data: Certain sensitive information is collected by businesses from their customers, which includes their date of birth, names, addresses, contact details, and financial information. Although all this information is needed to provide services and maintain customer relationships, it must be protected by the businesses from unauthorized access to ensure the privacy and safety of the customers.
To ensure confidentiality, integrity, and availability, individuals and organizations must identify sensitive data and classify it using appropriate measures. Organizations must carry out specific relevant data classification policies and procedures to identify which data is sensitive and classify it based on different categories to determine the proper level of protection and ensure it’s stored and transmitted securely.
The discussion of securing sensitive data has always been an issue among organizations and individuals, especially with the rise of cyberattacks and crimes like fraud, impersonation, etc. Securing sensitive data is essential to protecting individuals and businesses from these cyberattacks and other crimes, which can result in significant reputational and financial damage. Hence, individuals and organizations must prioritize data security and ensure their sensitive data is kept safe and transmitted securely.
In the next section, the fundamentals of data security are introduced, and different terms are defined.
The Fundamentals of Data Security
Some fundamental concepts must be discussed to ensure that sensitive data is kept safe.
Some of them are:
The CIA (Confidentiality, Integrity, and Availability) Triad
The CIA triad is a commonly accepted and used security model designed to guide organizations’ efforts in ensuring data security and forms the basis for developing secure systems.
- The C, which stands for confidentiality, refers to keeping sensitive data private and ensuring only authorized individuals can access it.
- The I, which stands for integrity, guarantees that information is accurate and correct and isn’t modified or tampered with.
- The A, which stands for availability, ensures authorized users can access data when needed. It includes providing information that’s available promptly and guaranteeing that the system and devices are up and running with minimal or no disruptions.
Encryption
Encrypting data is one of the most essential steps in data security. It involves converting plain data into a coded or unreadable format using an algorithm to scramble it so that only the key and password can decipher it. The most common types of encryption include hashing, symmetric, and asymmetric encryption.
Access Control Mechanism
This security measure limits access to sensitive data by implementing controls on who can view or perform specific actions on the data to maintain confidentiality.
Role-based access control (RBAC) and attribute-based access control (ABAC) are the most popular access control mechanisms.
The RBAC mechanism assigns permission to users in an organization based on their role. For example, an administrator in an organization will have more permission to execute certain acts than an ordinary user.
Unlike RBAC, which uses roles, ABAC uses attributes, also known as tags, to determine which users gain access to a resource. The labels can be based on the department, location, time, etc. For example, an organization might set a policy that only users with the tag “department=finance” can gain access to financial records.
Other access control mechanisms used in data security are Mandatory Access control (MAC), Discretionary Access Control (DAC), etc.
Authorization and Authentication
Although these two terms can be used interchangeably, differences and meanings exist. Authentication involves verifying the identity of a user before granting them access to a particular entity. It requires users to provide a unique identifier, such as a password, or biometric data, such as fingerprints. Other forms of Authentication include Two-factor authentication (2FA), Single Sign On System (SSO), and One-time passwords (OTP). While authentication verifies a user’s identity, authorization guarantees they only perform the actions and operations they can on that resource. These two terms are essential components of data security, and they provide adequate protection of sensitive data from unauthorized access and misuse.
Understanding these fundamentals like CIA, Encryption, Access Control Mechanism, Authorization, and Authentication will ensure organizations and individuals implement strong data security measures to protect sensitive data.
The following section focuses on the challenges and risks of data breaches.
The Risks and Challenges of Data Breaches
A “data breach” is an incident that occurs when sensitive data or protected information is accessed, viewed, or stolen by an unauthorized entity. It’s become significant in today’s digital world and poses a substantial risk to organizations and individuals. Attackers can use data leaked in a data breach for fraudulent activities and other malicious purposes.
Cybercriminals use phishing, malware, and social engineering techniques to access sensitive data. They launch attacks on software or hardware systems to steal data. Another reason for data breaches is human error. Employees may mistakenly send sensitive data to the wrong recipient or misconfigure the security settings, which can lead to sensitive leaks. Other reasons include weak security measures by organizations, insider threats, or physical theft.
The consequences that data breaches pose to an organization are severe, and there’s a need for organizations and individuals to be fully aware of these risks to mitigate them and defend themselves adequately against this attack.
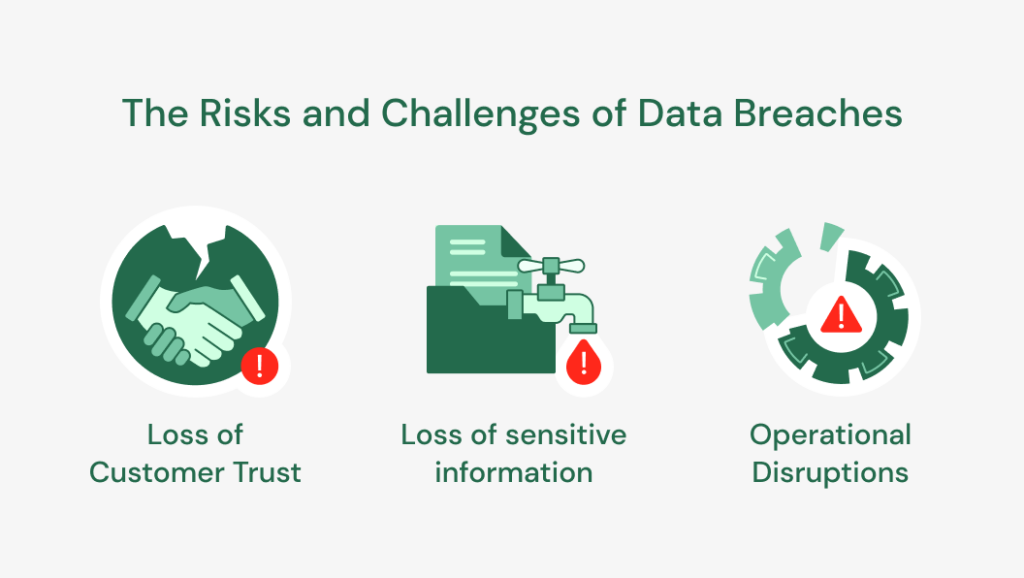
Some of the consequences include:
- Loss of Customer Trust: An organization leaking customers’ sensitive data can lead to customers losing confidence in their ability to keep them safe and protect their data. This can damage the reputation of the organization and lead to business losses.
- Operational Disruptions: Data breaches can lead to disruptions in an organization’s activities, as there might be a need to shut down specific systems to investigate the occurrence. This can lead to a loss of productivity and revenue.
- Loss of sensitive information: Data like financial records, personal information, and intellectual property are lost due to a data breach. Losing this information can harm the organization’s finances and reputation and make it less competitive.
Other consequences can include fraud, regulatory fines, financial loss, theft recovery costs, etc.
Organizations and individuals can proactively protect their sensitive data by being aware of these consequences.
The following section discusses the various ways and best practices in which organizations and individuals can ensure adequate data security.
Best Practices For Protecting Sensitive Data
The following are some of the best practices organizations and individuals can adopt to safeguard their data:
- Data discovery: To have a clear understanding of the data they own and who has access to it, organizations first need to know where all their data is by conducting regular data discovery exercises like data profiling, team questioning, data store scanning, and following data flows. Discovering data will help identify sensitive data and place the necessary controls over it.
- Secure Storage of Data: Security measures like encryption, access control, etc., should be implemented to ensure that sensitive data is stored securely.
- Securing Data Transmission: Data leaks and breaches occur when transmitting data. Organizations should ensure sensitive data is transmitted safely over networks to prevent this. The networks can use Transport Layer Security (TLS) for web traffic or private virtual private networks (VPNs) to secure remote access during data transmission.
- Data Monitoring: Organizations should track their data regularly by checking past activity, log files, etc., in their systems. Modern technologies even allow runtime monitoring of data – from data creation through the applications that process it until storage. Monitoring data can help quickly identify unusual activity, a potential security incident, and how to best remediate a data violation.
- Data Classification: Data can be classified based on its sensitivity and regulatory requirements so that the right security controls are placed on it.
Using a Data Security Platform: Data security platforms like Flow Security are used to control all organizational data, including shadow data stores and applications, across all cloud, on-prem, and SaaS environments. Such platforms automatically identify and classify sensitive data (e.g., PII, PHI, PCI), detect and remediate data risks, and effectively respond in real-time to data violations.
Other best practices include
- Access Control
- Regular data backups
- Data retention and disposal policies
- Employee Training and Awareness
Exploring Flow Security: A Data Security Platform
Flow Security is a comprehensive data security platform that provides various solutions to help organizations protect their sensitive data. It helps organizations discover, classify, and protect their data on the cloud, on-premises, and shared externally.
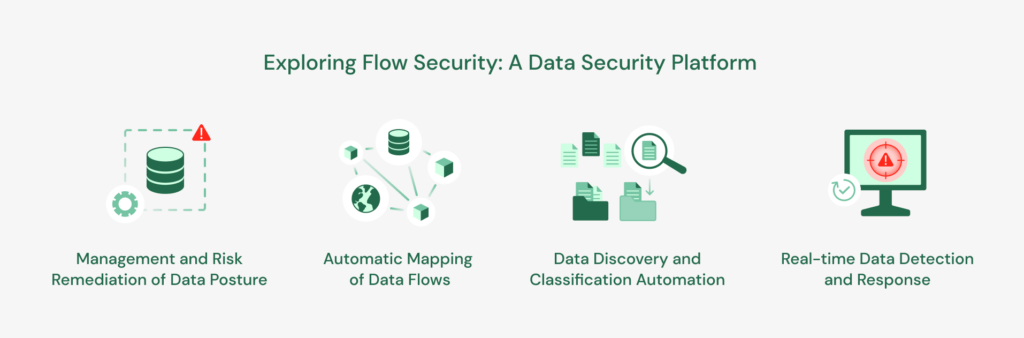
Flow Security’s solutions include:
- Data Discovery and Classification Automation: Flow Security automates the discovery and classification of data, providing a comprehensive view of all the organization’s data. It then automatically classifies and builds a catalog of all sensitive data (e.g., PII, PHI, PCI).
- Automatic Mapping of Data Flows: Flow Security automatically maps data flows across an organization’s network, discovering all kinds of data and providing insights into data processing, shadow data stores, and data flows.
- Risk Remediation and Management of Data Posture: Flow Security provides a centralized dashboard that enables organizations to manage their security posture and remediate risks.
- Real-time Data Detection and Response: Flow security provides real-time detection and response to security incidents, enabling organizations to respond quickly to threats by providing the full context: who, what, when, where, and why.
In conclusion, protecting sensitive data is crucial for any organization that wants to safeguard data against breaches and cyber-attacks. In this article, we explored what sensitive data is and its common examples, the fundamentals of data security, the risks and challenges of data breaches, and the best practices for protecting sensitive data.
Various technologies, such as encryption and access control mechanisms, can help protect data. However, more is needed to identify and classify sensitive data to know which controls to place and effectively respond in the event of a data breach. Organizations need data security platforms like Flow Security to remediate risks and accurately respond to security incidents.