PCI DSS Compliance Services: Safeguarding Cardholder Data
Payment Card Industry Data Security Standard (PCI DSS) compliance is a set of security standards designed to protect cardholders’ information and prevent fraud. In this article, we will discuss the importance of PCI compliance services for businesses that handle transactions via card and provide an overview of the solutions and services available to ensure compliance.
Why Did PCI DSS Come About?
As cyber criminals began creating new ways to infiltrate card payment systems and payment networks, the major credit card companies – Discover Financial Services, American Express, JCB International, Mastercard, and Visa – came together to create the Payment Card Industry Data Security Standard (PCI DSS). This standard composed a set of security requirements for merchants or businesses to protect their customer’s cardholder information and prevent fraud. With the help of PCI compliance services and solutions, businesses can ensure they are meeting the required standards easily and effectively.
Overview of PCI DSS Services and Solutions
PCI DSS compliance services and solutions are intended to aid merchants in achieving and maintaining PCI DSS compliance. These services usually include:
- PCI compliance assessments: These involve a comprehensive evaluation of a business or organization’s security practices to identify risks and ensure they comply with PCI standards.
- Penetration testing: This involves simulating attacks on an organization or business system to identify any weakness or loophole that could be exploited by a hacker.
- Tokenization: This involves replacing sensitive cardholder information with a non-sensitive “token” that can be used to handle transaction processes.
- Encryption: This involves converting sensitive information into a format that is not readable until decrypted with a key. This reduces the risk of sensitive data being stored or transmitted in plain text.
Why PCI DSS Compliance is Crucial for Businesses that Accept Card Transactions
PCI compliance is an essential requirement for any business that accepts payment via card. In a case of a breach and a company is found to be non-compliant, they risk the loss of doing business with the payment card providers. PCI compliance has become a critical standard for businesses of all sizes; by complying with PCI requirements and standards, businesses can demonstrate a commitment to protecting their customer’s data which is crucial in recent times when customers are more concerned about the security of their data, which in turn will build trust and loyalty. Failure to comply with PCI standards can result in fines, legal fees and can cause damage to a business or organization’s reputation.
PCI DSS Compliant Mandate
The PCI compliance mandate is a set of requirements that are established by the Payment Card Industry Security Standards Council (PCI SSC) that all organizations handling payment card data must follow. The requirements were designed to create a secure environment for payment card data, reduce the risk of data breaches and fraud, and protect consumers from financial harm.
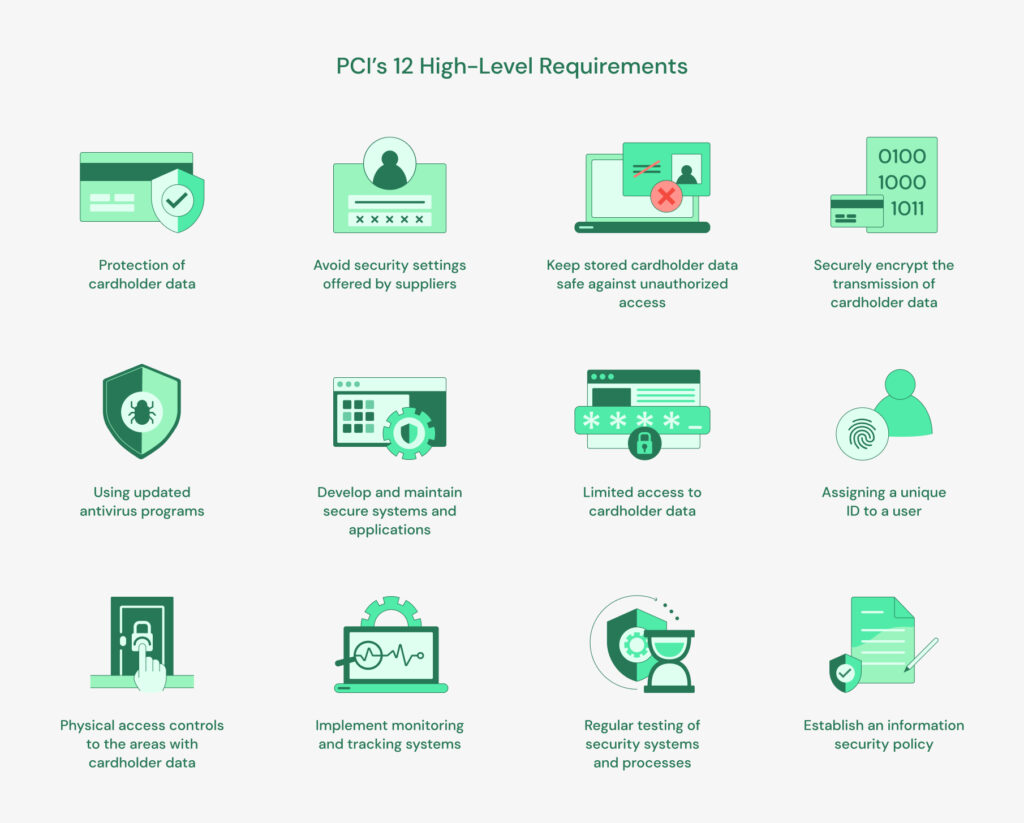
Access control, monitoring, and encryption are only a few of the security procedures that are covered by the PCI’s 12 high-level requirements and which are as follows:
- Implement and maintain a firewall system to protect cardholder data.
- Avoid using default system passwords and other security settings offered by suppliers.
- Keep stored cardholder data safe against unauthorized access.
- Securely encrypt the transmission of cardholder data over open and public networks.
- Making use of updated anti-virus programs.
- To prevent vulnerabilities, develop and maintain secure systems and applications.
- Access to cardholder data should be limited based on business need-to-know.
- Each user with computer access should be assigned a unique identifier.
- Areas where cardholder data is processed or stored are subject to strict physical access controls.
- Implement thorough monitoring and tracking systems for all network assets and cardholder data access.
- Conduct regular testing of security systems and processes to identify and address vulnerabilities.
- Establish an information security policy that applies to every person within the organization.
Description of PCI DSS Controls
Although the PCI high-level requirements and PCI Controls are related, they are not the same. While the PCI high-level requirements are a set of 12 security goals that must be met by an organization to be compliant, the PCI controls are certain steps or procedures an organization can take to satisfy those requirements.
Each of the 12 high-level requirements is broken down into sub-requirements, which are, in turn, broken down into specific controls. For example, the second requirement, “Do not use vendor-supplied defaults for system passwords and other security parameters,” includes sub-requirements such as “Remove/disable unnecessary default accounts and passwords” and “Change all vendor-supplied default passwords and security parameters.”
Each of these sub-requirements is then broken down into specific controls that organizations can implement to meet the requirement. For example, the “Remove/disable unnecessary default accounts and passwords” control might include a sub-requirement like “Remove all unnecessary user accounts from systems and applications.”
Key Changes and Updates in the Latest Version of PCI DSS Compliance
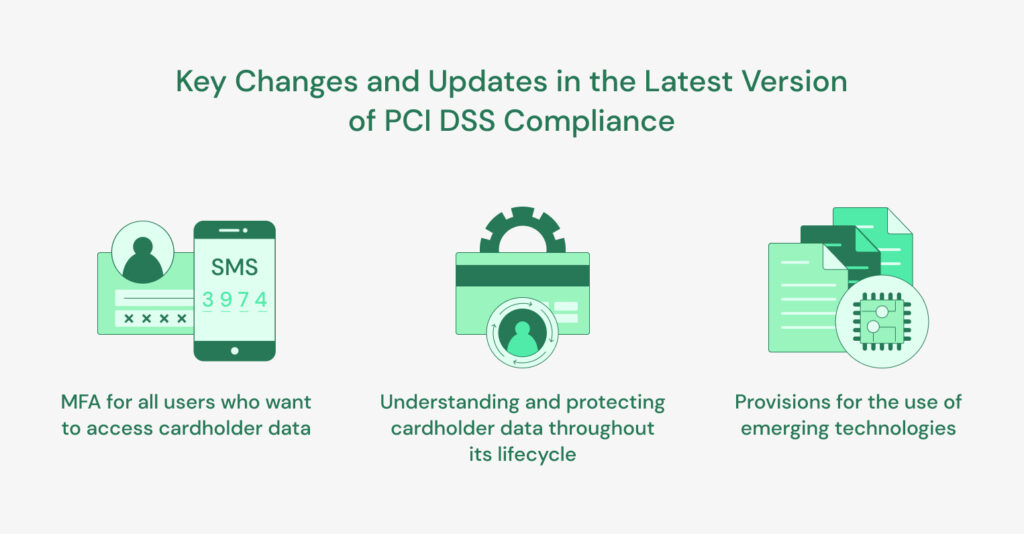
The latest version of the Payment Card Industry Data Security Standard (PCI DSS) introduces several new requirements and updates to existing ones to make card payment transactions more secure and better protected against cyber threats.
One of the major updates in PCI compliance 4.0 is an increased focus on data control. This new update places greater emphasis on the importance of understanding and protecting cardholder data throughout its lifecycle. Another noticeable update would be the use of multi-factor authentication (MFA) for all users who want to access cardholder data.
Together with the increased focus on data controls, the updated PCI compliance standard also recognizes the importance of innovation and new technologies in the payment card industry. The new standard includes provisions for the use of emerging technologies such as mobile payments, contactless payments, cloud-based solutions, etc., provided that appropriate security measures are in place to protect cardholder data.
PCI Compliance 4.0 represents a major step forward in the ongoing effort to protect payment card data from theft and fraud. By focusing on data controls and placing a greater emphasis on risk management, the new standard helps ensure that organizations are doing everything possible to protect their customer’s valuable information.
Data Controls to Achieve PCI Compliance
Data controls are critical components of achieving PCI compliance, as they help organizations protect their customer’s payment card data against theft and other security threats. Let’s take a closer look at some of the key data controls required to achieve PCI compliance.
Data Discovery: This involves identifying the locations where cardholder information is being stored, processed, and transmitted within an organization.
Data Classification: This involves providing labels to cardholder data once discovered; the labeling is done depending on its level of sensitivity where accessible data is made public and data not meant for public consumption are labeled confidential.
Data Monitoring: This involves using tools that may include log analyzers, intrusion detection systems, data security platforms, and many other prominent tools that are used to detect where data resides and is moving as well as any unauthorized usage or access.
Data Segregation: This involves keeping data in separate databases and systems that are dedicated solely to payment card processing to limit the risk of data compromise.
Access Controls: This ensures that only authorized individuals have access to cardholder information. These measures can include two-factor authentication, role-based access, and many more.
Data Encryption: This ensures that cardholder information is encrypted and protected against unauthorized access, even if this information falls into the wrong hands. Data is encrypted at rest and in transit.
Compensating Controls: Sometimes, it may not be possible to implement all required data controls due to certain limitations (technical or operational). In such cases implementing compensating controls to provide optimal security for any missing controls becomes crucial.
By implementing these key data controls, organizations can significantly reduce the risk of payment card data theft and fraud and achieve PCI compliance. While this may require a significant investment of time and resources, the benefits of protecting customer trust, avoiding costly breaches, and ensuring business with the major payment card providers, make it well worth the effort.
Going Beyond PCI DSS to Achieve a True Data Security Strategy
Using PCI DSS as a Springboard for a Data Security Strategy
The Payment Card Industry Data Security Standard (PCI DSS) provides a solid foundation for protecting payment card data, but it should not be the only focus of an organization’s security strategy. One way to use PCI as a springboard for a broader data security strategy is to start by addressing the gaps in an organization’s compliance posture by conducting a comprehensive assessment to identify areas where an organization falls short in security and specifically, of the PCI DSS requirements. This can help prioritize and allocate resources more effectively to achieve compliance.
Another way to go beyond PCI is to adopt a more proactive and risk-based approach by conducting regular risk assessments, developing a stringent data security strategy, incident response plans, and investing in advanced security technologies such as data security platforms.
The additional value you receive is that leading by a sound data security strategy, as opposed to leading by a regulation or mandate, means that you’re for the most part covered for other regulations and mandates as well. This means that instead of being in a chase to achieve compliance, you typically already have most of the required controls.
Building Towards a Mature Data Security Strategy
A mature data security strategy requires a comprehensive approach that covers all aspects of an organization’s operations. Achieving this level of maturity requires a sustained effort and investment in security measures. To build toward a mature data security strategy, organizations need to focus on several key areas, such as:
- People
- Processes
- Technology
- Continuous Improvement
Conclusion
In today’s ever-evolving environment, maintaining the highest levels of security is essential for businesses of all sizes; PCI compliance is an important requirement for any business that handles card payment transactions. By putting the required controls in place and adhering to PCI DSS requirements, an organization can protect its customer’s sensitive information and uphold the trust of its customers.
It is important to note that PCI is just the beginning or more of a starting point. Organizations can build a complete and comprehensive data security strategy by going above what the PCI rules offer which in turn can provide better protection against a wider range of security threats


