Efficiently Obtain PCI DSS v4.0 Evidence with Flow Security
Introduction
Handling credit card data is a serious business. An organization that mishandles this type of information doesn’t just risk angry consumers, it will also face grave legal, financial and regulatory ramifications.
The payment card industry (PCI) does not take this endeavor lightly – holding organizations to a stringent set of data security standards (PCI DSS). Failing to keep up with these regulations can incur significant financial loss and reputational damage. Although the motivation is strong, ensuring a business is fully PCI DSS compliant is often challenging and incredibly time-consuming.
In this blog post, we take a look at what it means to be PCI DSS compliant and examine the key aspects that should be incorporated into your data security strategy. We then demonstrate how Flow Security’s unique data security platform provides crystal-clear visibility of your PCI data and helps ensure your business is fully PCI compliant from end to end.
Why PCI DSS Matters
Non-compliance with PCI-DSS regulations can lead to heavy fines, weaken your credibility and wreak havoc on your business. Depending on the size of your company and the degree of non-compliance, penalties can range from $5000 to $100,000 per month. Put another way, fines per security breach can reach a staggering $500,000. But the damage doesn’t stop there.
In the event of a breach, companies are obliged to notify the individuals whose cardholder data may have been leaked, incurring additional costs. Add on to this reputational damage, costly audits and potential lawsuits and you get a cocktail of trouble.
Let’s take a look at the latest guidelines designed to keep your business compliant and thriving.
Introducing PCI DSS Regulations – Version 4.0
So how do we ensure we are PCI compliant?
There are 12 high-level requirements to help guide us. These are designed to create a secure environment for payment card data, reduce the risk of data breaches and fraud, and protect consumers from financial harm.
In March 2022, the Security Standard Council issued an updated version (4.0) that places greater emphasis on understanding and protecting cardholders’ data throughout its full lifecycle. More specifically, the report stresses the importance of data control, a crucial element of PCI compliance.
These controls include:
- Data discovery and classification – creating a data inventory and identifying where your PCI data is.
- Data monitoring and segregation – creating an up-to-date data-flow diagram of the environment, as well as a segregated area where PCI data is handled and stored.
- Data encryption – making sure all PCI data is encrypted both in transit and at rest.
By implementing these controls, organizations can meet the necessary requirements for PCI compliance. Doing so, however, is easier said than done.
In the next section we walk you through Flow’s solution and demonstrate how it enables companies to regain control of their PCI data and meet regulatory requirements with maximum speed and minimum hassle.
Making PCI Compliance Simple and Efficient with Flow Security’s Solution
As we’ve seen above, upholding PCI DSS regulations is not a trivial matter. Ensuring your organization meets compliance requirements can take considerable time and resources. Any tiny oversight can lead to data loss and breaches, together with hefty fines and financial penalties.
Flow Security offers a holistic approach to data security by classifying and monitoring data in general and PCI data in particular. By combining data scanning and data flow analysis in real time, Flow empowers companies to secure sensitive data by managing policies and remediating data-related risks. This helps organizations get the necessary evidence needed to comply with PCI compliance easily and efficiently.
Let’s dive deeper into how Flow does this.
Discovery, Classifications and Data Mapping
First – to secure it, you’ve got to know it’s there.
Flow Security’s platform allows organizations to automatically discover all the data that flows in and out of their environment. It inspects and classified data both in motion and at rest, using smart classification algorithms to tag sensitive data, including (but not limited to) credit card information and more.
By tracking sensitive data as it flows between the different components in the environment, Flow provides visibility not only of where sensitive data is being stored, but also of where it is sent (and where it has come from). This allows you to access the full data lifecycle, a capability that is especially crucial with regard to external services and external databases that may process or store PCI data.
With just one click you can export data-flow diagrams of your sensitive data, ensuring it is fully secured as it flows in and out of your environment.
A full map of the environment
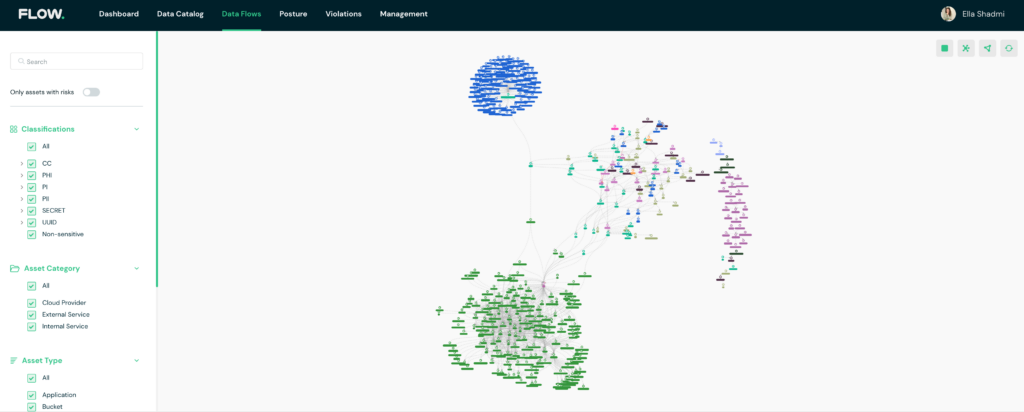
A full data catalog of the environment
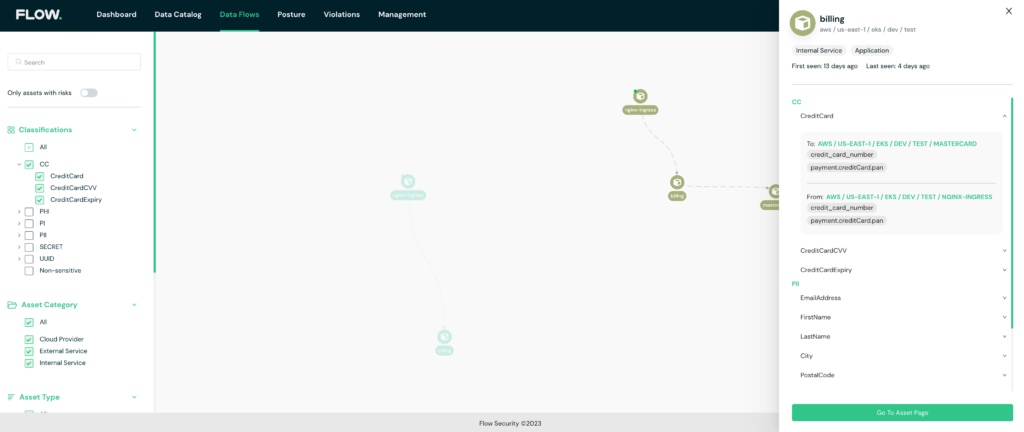
The PCI environment
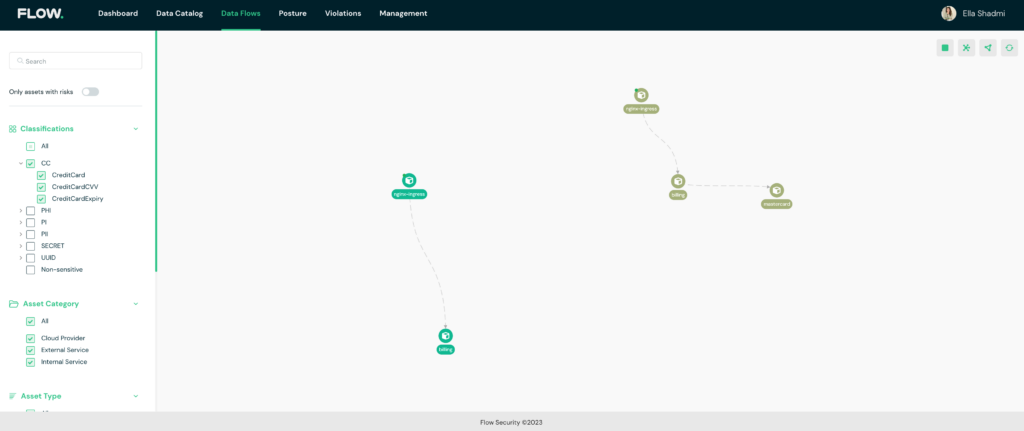
Data-flow diagram
Actionable Evidence in One Click
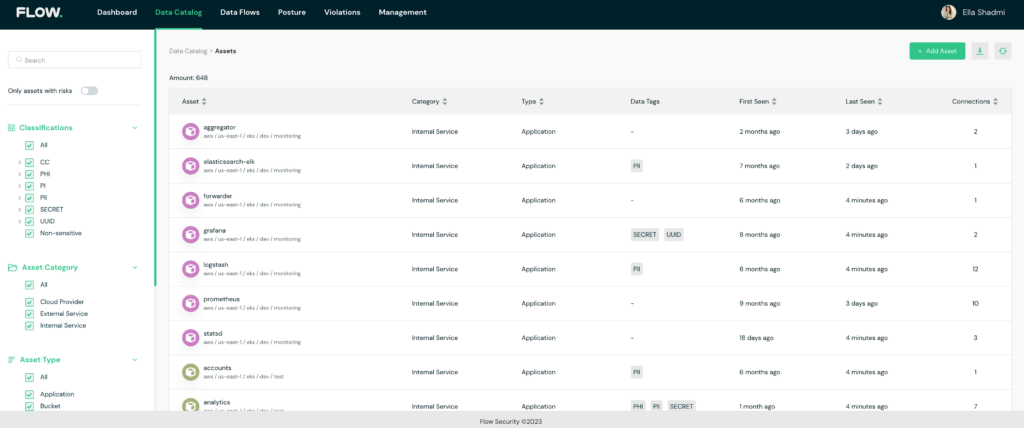
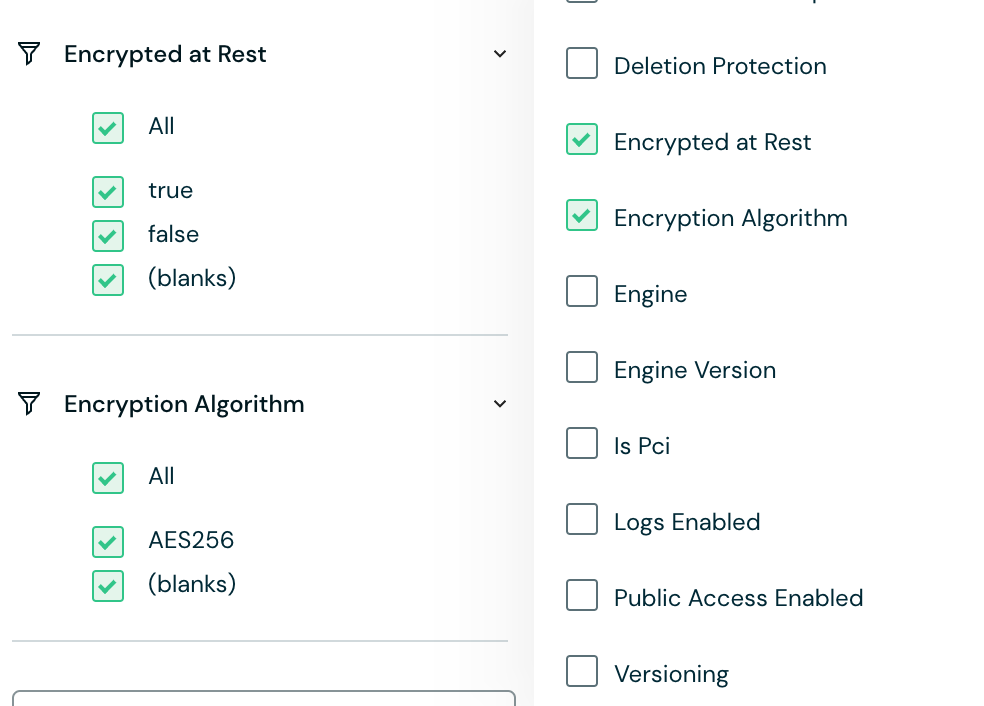
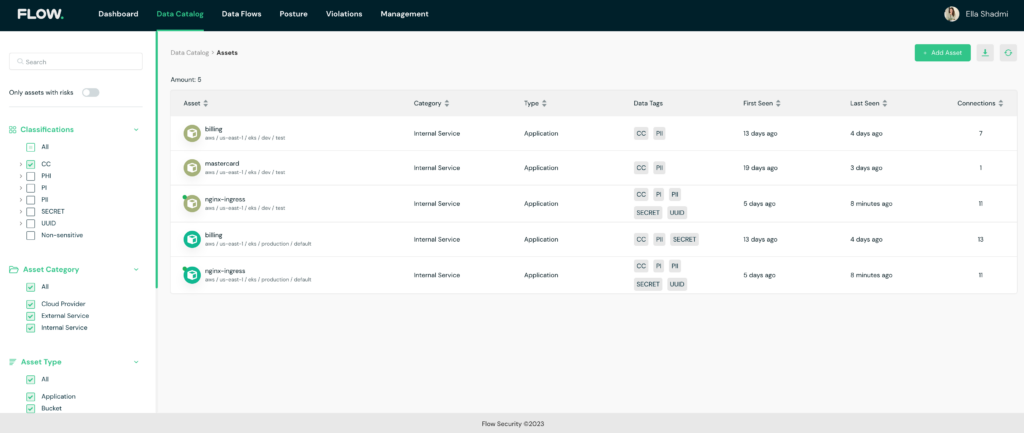
The platform’s smart classification engine allows for easy filtering and exporting of cardholders’ data (CHD) and sensitive authentication data (SAD) inventory. With Flow, you can monitor all assets in the environment through a detailed data catalog, enriched by added properties and metadata. This level of visibility and monitoring allows you to, for example, ensure that card data is encrypted when transmitted over open and public networks.
Encryption filtering
Data catalog for PCI environment
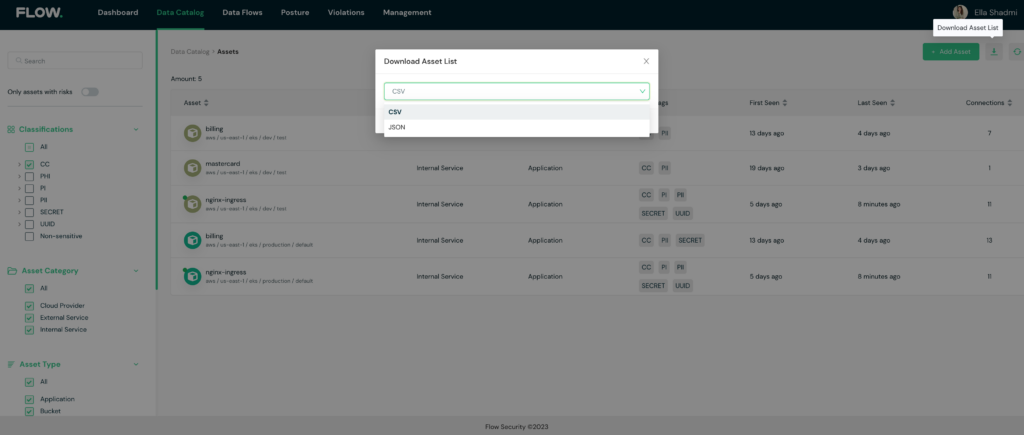
Export options
Data Monitoring and Control
Once you have a data flow diagram that details where cardholders’ data (CHD) flows, you are ready to take active steps to secure it.
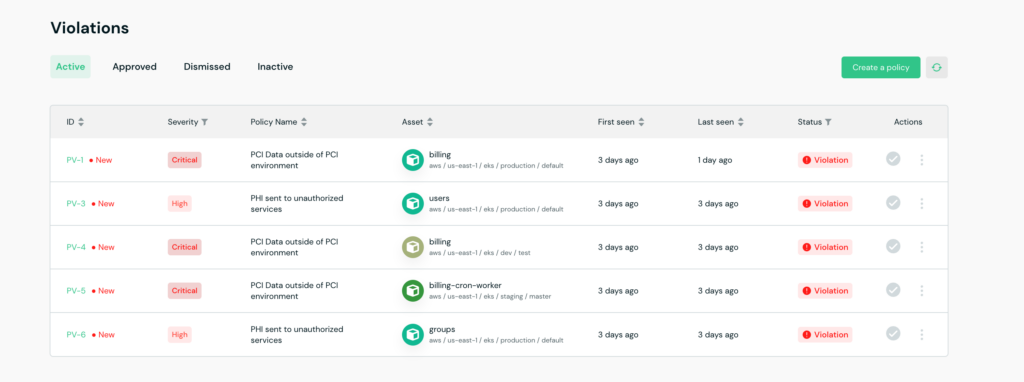
This is where things get really interesting. With Flow, you can create customized policies to control where data is transferred and stored and flag violations such as PCI data that leaves its dedicated environment.
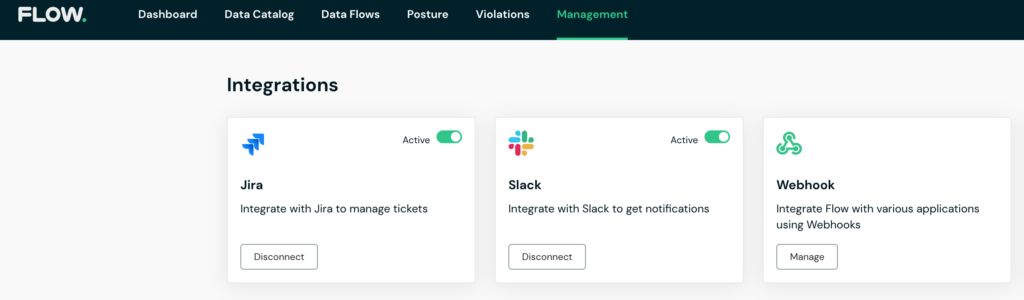
In the event of a violation, you’ll be notified immediately, and receive relevant information to conduct a swift investigation and remediation. To ensure maximum efficiency and zero friction with existing workflows, Flow integrates directly with a wide variety of alerting systems, ticketing platforms, and customizable webhooks.
Creating a customized policy
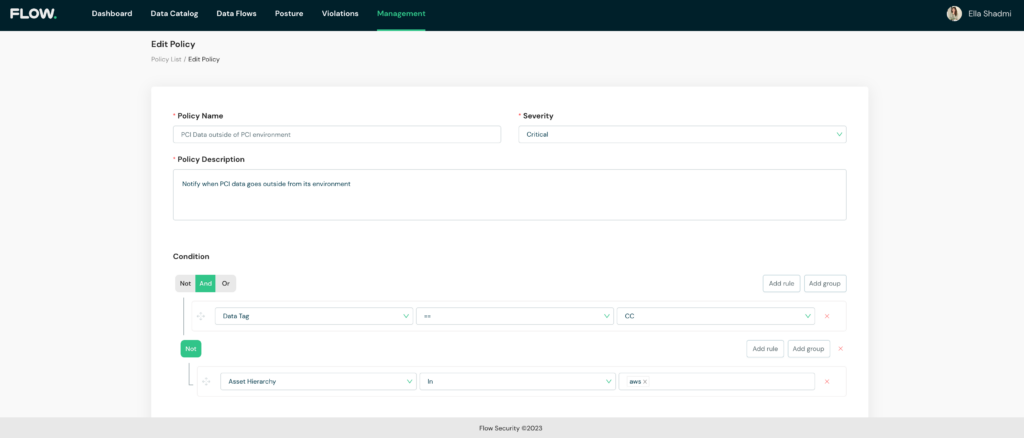
Violation alerts for PCI data outside of the designated environment
Integration to your internal workflows
Start Preparing for your PCI DSS Audit Compliance Now
PCI data is a sensitive topic. While we all want our technology to run like clockwork – we also want to sleep easy at night. Organizations have a duty to consumers, their strategic partners, and themselves to take every measure to secure credit card data. This isn’t easy to do, especially as modern environments become increasingly complex.
This is precisely why we’ve created Flow. With just a few clicks, you can generate crucial PCI DSS evidence and ensure you tick every box on the Security Standard Council’s list of requirements, efficiently and hassle-free. Don’t wait until the last minute – secure data wherever it flows today.